What is MCP?
Model Context Protocol (MCP) enables Firebender to connect to external tools and data sources.Why use MCP?
MCP connects Firebender to external systems and data. Instead of explaining your project structure repeatedly, integrate directly with your tools. Write MCP servers in any language that can print tostdout or serve an HTTP endpoint: Python, JavaScript, Go, etc.
How it works
MCP servers expose capabilities through the protocol, connecting Firebender to external tools or data sources. Firebender supports three transport methods:| Transport | Execution environment | Deployment | Users | Input | Auth |
|---|---|---|---|---|---|
stdio | Local | Firebender manages | Single user | Shell command | Manual |
SSE | Local/Remote | Deploy as server | Multiple users | URL to an SSE endpoint | OAuth |
Streamable HTTP | Local/Remote | Deploy as server | Multiple users | URL to an HTTP endpoint | OAuth |
Protocol support
Firebender supports these MCP protocol capabilities:| Feature | Support | Description |
|---|---|---|
| Tools | Supported | Functions for the AI model to execute |
Installing MCP servers
One-click installation
Install MCP servers from our collection and authenticate with OAuth.Using mcp.json
Configure custom MCP servers with a JSON file:
CLI Server - Node.js
CLI Server - Python
Remote Server
STDIO server configuration
For STDIO servers (local command-line servers), configure these fields in yourmcp.json:
| Field | Required | Description | Examples |
|---|---|---|---|
| type | Yes | Server connection type | "stdio" |
| command | Yes | Command to start the server executable. Must be available on your system path or contain its full path. | "npx", "node", "python", "docker" |
| args | No | Array of arguments passed to the command | ["server.py", "--port", "3000"] |
| env | No | Environment variables for the server | {"API_KEY": "${env:api-key}"} |
| envFile | No | Path to an environment file to load more variables | ".env", "${workspaceFolder}/.env" |
Configuration locations
Project Configuration Createfirebender.json in your project directory for project-specific tools.
Global Configuration
Create ~/.firebender/firebender.json in your home directory for tools available everywhere.
Config interpolation
Use environment variables in your configuration values. Firebender resolves variables in these fields:command, args, env, url, and headers.
Supported syntax:
${VAR_NAME}- Environment variable with braces$VAR_NAME- Environment variable without braces
Local Server
Remote Server
Authentication
MCP servers use environment variables for authentication. Pass API keys and tokens through the config. Firebender supports OAuth for servers that require it.Using MCP in chat
Firebender Agent automatically uses MCP tools listed underAvailable Tools when relevant. Ask for a specific tool by name or describe what you need. Enable or disable tools from settings.
Toggling tools
Enable or disable MCP tools directly from the chat interface. Click a tool name in the tools list to toggle it. Disabled tools won’t be loaded into context or available to Agent.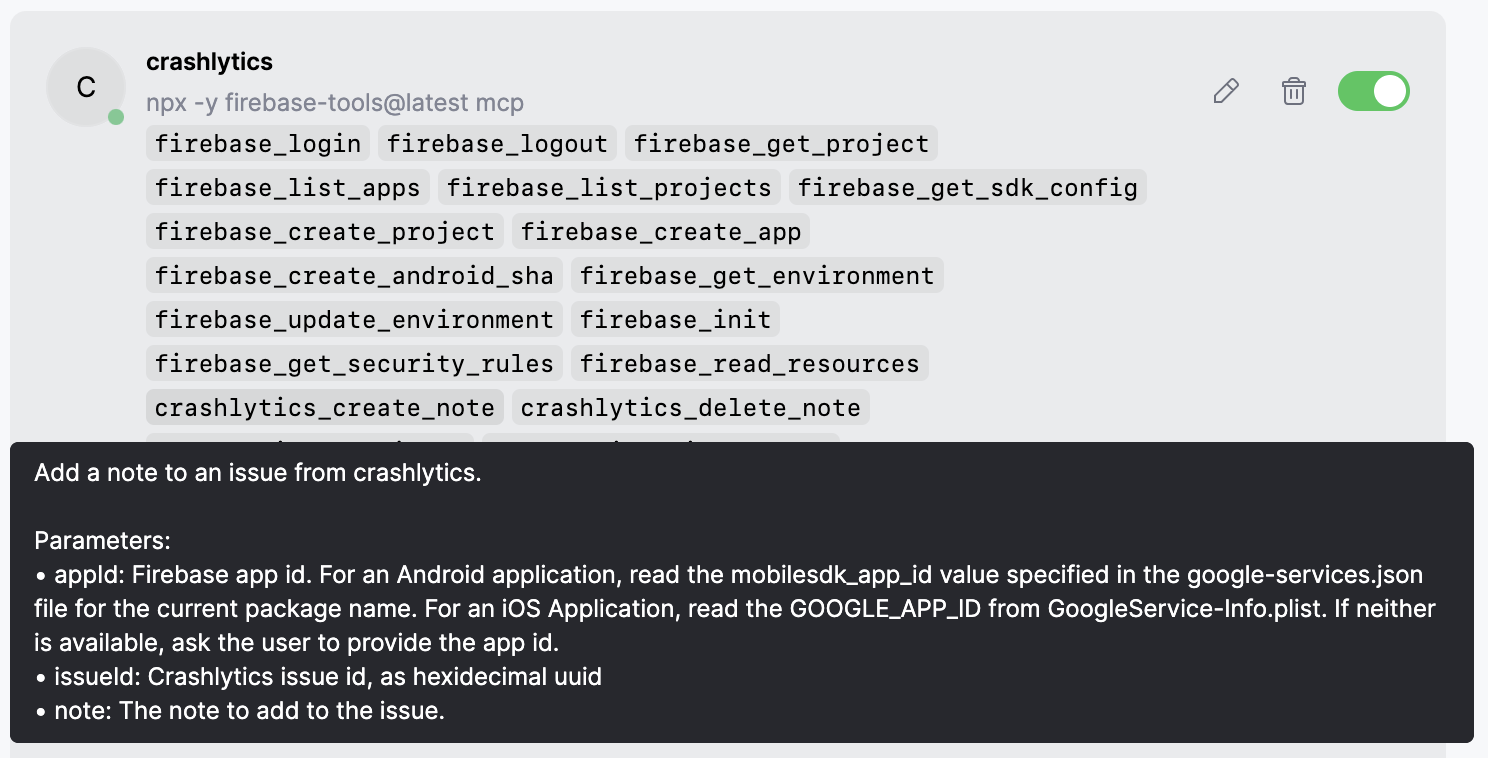
Tool response
Firebender shows the response in chat with expandable views of arguments and responses.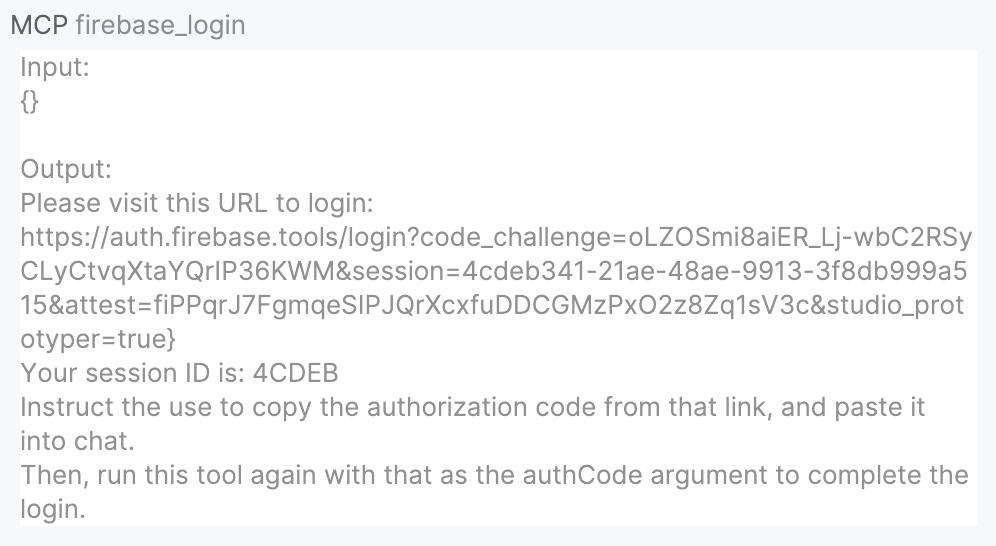
Images as context
MCP servers can return images: screenshots, diagrams, etc. Return them as base64 encoded strings. Firebender attaches returned images to the chat. If the model supports images, it analyzes them.Deferred tool loading
By default, MCP tools load on-demand to save tokens. Only setdeferLoading: false for orchestration MCPs that modify core agent behavior. Keep the default for service integrations (databases, APIs, monitoring). See the configuration reference for details.
Security considerations
When installing MCP servers, consider these security practices:- Verify the source: Only install MCP servers from trusted developers and repositories
- Review permissions: Check what data and APIs the server will access
- Limit API keys: Use restricted API keys with minimal required permissions
- Audit code: For critical integrations, review the server’s source code
FAQ
Why doesn't the remote Figma MCP work?
Why doesn't the remote Figma MCP work?
Remote Figma MCP (
mcp.figma.com) doesn’t support Firebender yet. Use Figma Desktop instead. Want remote? Comment here and email Figma.What's the point of MCP servers?
What's the point of MCP servers?
MCP servers connect Firebender to external tools like Google Drive, Notion, and other services to bring docs and requirements into your coding workflow.
How do I debug MCP server issues?
How do I debug MCP server issues?
View MCP logs by clicking the plug icon in the chatbox and selecting “Open MCP Log”: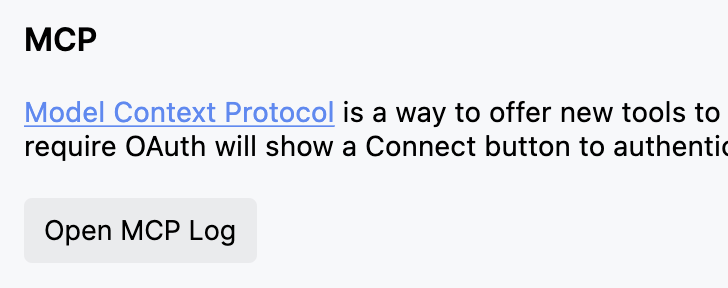

Can I temporarily disable an MCP server?
Can I temporarily disable an MCP server?
Yes! Toggle servers on/off without removing them by clicking the plug icon in the chatbox to manage the servers. You can enable or disable any MCP server from the dropdown.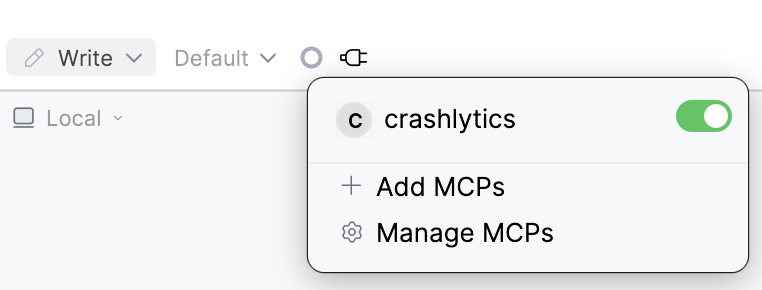

What happens if an MCP server crashes or times out?
What happens if an MCP server crashes or times out?
If an MCP server fails:
- Firebender shows an error message in chat
- The tool call is marked as failed
- You can retry the operation or check logs for details
- Other MCP servers continue working normally
Can I use MCP servers with sensitive data?
Can I use MCP servers with sensitive data?
Yes, but follow security best practices:
- Use environment variables for secrets, never hardcode them
- Run sensitive servers locally with
stdiotransport - Limit API key permissions to minimum required
- Review server code before connecting to sensitive systems
- Consider running servers in isolated environments